Artificial Intelligence (AI) has, as in every industry, long been discussed at length in the intelligence community as both a potential gamechanger and a potential risk. Business leaders across all sectors have been eager to harness the potential of AI, viewing it as potentially transformational for their organizations. Many employees in junior or operational roles, however, are perhaps more likely to view the technology with some apprehension, seeing it either as something that could add complexity to their work or as a tool that might ultimately replace their roles. For the intelligence sector specifically, concerns persist about deepfakes and weaponized disinformation campaigns powered by AI, which complicate OSINT collection and necessitate additional layers of verification in the intelligence cycle.
Despite these concerns, the potential of AI is enormous – and the technology is clearly here to stay. This creates both an opportunity to master its use and leverage it as a tool, and a risk of falling behind for those who choose to dismiss it. Just as AI can be a disruptive tool in the hands of malicious actors, it can also be a powerful asset for threat intelligence analysts in overcoming these challenges, simplifying workflows and eliminating existing inefficiencies.
This blog will spotlight the role that AI can play in terms of threat intelligence, its impact on the role of the human analyst, and the ways in which it can make their jobs much easier.

AI can be a useful tool for threat intelligence analysts
The first thing that intelligence analysts should understand is that AI is not going to make their role obsolete any time soon. Human-led intelligence is still a vital part of making sure that information is accurate, actionable, and trustworthy.
As we have written in the past, emphasizing speed in your intelligence collection efforts should be a key priority – but without any context or built-in analysis to this information you could actually be costing yourself time. An automated feed of data gathered by AI and datamining algorithms can get data in front of you quickly, but without a human expert to decipher it, that’s all that information is – raw data, with none of the tailored intelligence, verified information or actionable insights that allow our clients to act quickly on accurate intel.
The benefit of advanced generative Large Language Models (LLMs) like ChatGPT is that AI can now, in theory, add this context to the data it receives. Still here a level of human expertise is required. So-called ‘hallucinations’ – where an AI creates information that seems real, but isn’t accurate or true – mean that an expert eye is required to identify when something doesn’t seem right. These instances of AI ‘making things up’ can vary in frequency: anything from 3% to 27% depending on the system used, according to one study. While 3% might seem low, in a high-stakes industry like threat intelligence any inaccuracies could be crucial, potentially being the difference between accurate advice and a highly consequential mistake. Intelligence analysts – already adept at spotting and filtering out fake news – will be well placed to do the same with AI hallucinations, too.
That being said, AI has the potential to vastly improve the work intelligence analysts are doing, too.

AI’s ability to quickly process large volumes of threat intelligence data can save analysts valuable time and resources
While, as noted above, issues such as AI deepfakes and disinformation campaigns can make intelligence collection a more difficult and complicated process, AI can also be used to identify these fakes. Tools such as Sentinel have been praised for the ways in which they can detect deepfakes with both accuracy and speed, easing the process of identifying fake media and allowing analysts to report incidents with greater confidence and accuracy.
AI can also be used to solve – or at the very least ease – problems that have plagued intelligence analysts for a much longer time than deepfakes. The problems of the ‘Four V’s’ of data – Volume, Variety, Velocity and Veracity – can all, in some ways, be assisted by AI tools.
One such problem is the issue of too much information. While having access to as much data as possible should, in theory, be a good thing for intelligence collection, the issue is that processing such vast amounts of information is impractical given the number of analysts it would require and the time that it would take. This is where an AI tool that can quickly read, process and summarize information can help. AI can process large volumes of unstructured data from diverse sources and organize it into structured formats for easier analysis by the analyst – exploiting its data processing capabilities without removing the human expert from the equation.
Further enhancing an analyst’s research capabilities is AI’s ability to act as a search tool, as a facilitator for monitoring global developments through its multi-language capabilities, and as a useful sounding board across all elements of the intelligence cycle – from providing historical context and background information to inform initial collection efforts, to highlighting particular elements that different individuals might be most interested in, which analysts can focus on ahead of dissemination.
AI also excels at identifying patterns and trends from historical data – this makes it an excellent tool for flagging common indicators of past security risks and allowing the analyst to proactively address any emerging threats that mirror these patterns. It also means that AI is well-suited for sentiment analysis modeling through social listening; because of the capabilities of LLMs to understand context and emotional tone, this can avoid previous limitations where, for instance, a post talking about a ‘killer breakfast’ might be flagged for negative sentiment and lead to irrelevant data inundating the human analyst.
By filtering noise, prioritizing high-value data, and performing previously mundane, time-consuming tasks at speed, AI can also reduce the cognitive burden on analysts, enabling them to focus on higher-value analysis and decision making. This ability to provide analysts with quick insights is a tangible benefit that can not only aid analysts collecting intelligence – such as those who make up the 24/7 operations team who populate our platform – but also assist in quickly understanding large volumes of threat intelligence data, as the users of the S7 ONE platform might frequently find themselves being presented with.
This issue of high-volume, granular information is why we have incredibly in-depth filtering capabilities on the platform, so that our clients can easily break down our threat intelligence data to find the exact information that is relevant to their operational needs. By using AI, we can take this one step further.
Introducing the Virtual Analyst tool on the S7 ONE platform
Our new AI-driven Virtual Analyst tool does exactly that, by providing instant summaries of selected data, detailing key elements such as incident types, geographical distribution, and emerging trends. By streamlining the process of contextualizing raw data, analysts are better equipped to make timely and informed decisions.
How it works is simple – populate your filter, search for the incident data that you’re most interested in, and then select the Virtual Analyst tool to instantly summarize what you’re seeing. For example, let’s say you wanted to quickly understand the last seven days of protest that had taken place in your country of operation. In this instance you can filter for the exact time period you’re interested in, the country you wish to know about, and the category of incident – in this case, protest.
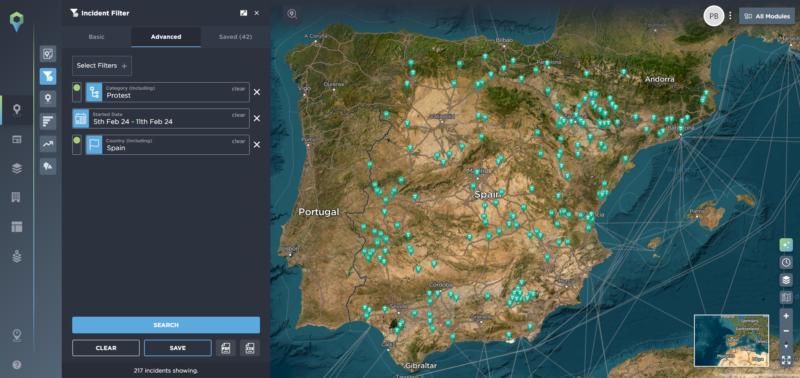
Filtering for a seven day period of protest on the S7 ONE platform
As you can see, for the filter we’ve selected here, you would be presented with hundreds of individual incidents that have been mapped by our analysts. Gaining a clear picture of events might take a considerable amount of time as you work your way through the incidents.
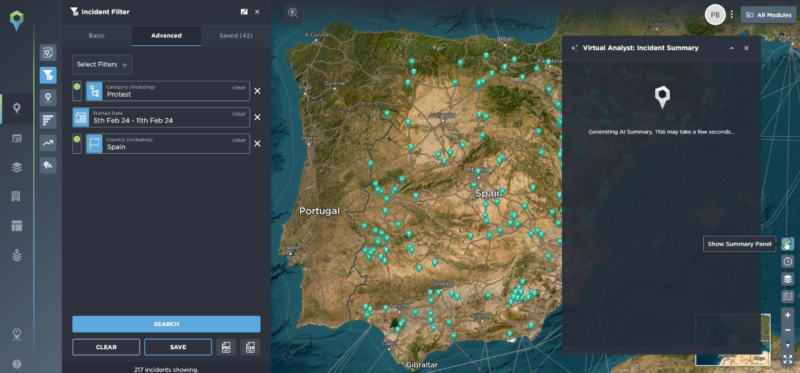
Clicking the show summary panel button on the right hand side of the screen will trigger the Virtual Analyst to generate a summary of the data in seconds
Instead, you can get a head-start on this by clicking the Virtual Analyst symbol in the bottom right of the screen. In a matter of seconds, you are presented with a detailed summary of the incidents, giving you a clear understanding of where to begin your analysis, and saving your team time and resources that would otherwise have been spent unpicking the data.
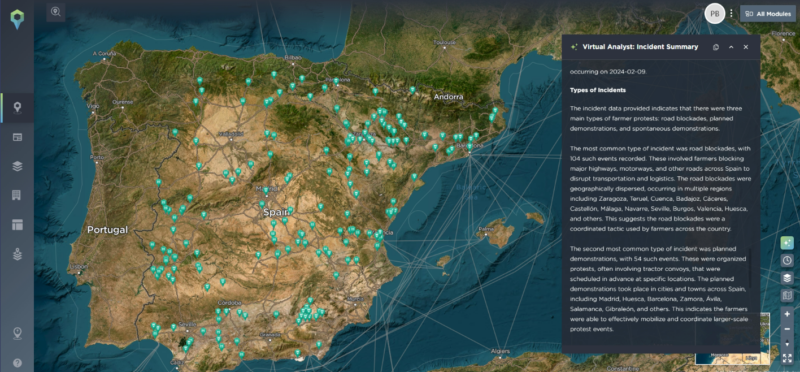
The Virtual Analyst’s AI-driven summary is powered by our human-verified threat intelligence data, reducing the risk of inaccurate information
Users can quickly identify trends and patterns highlighted by the Virtual Analyst, which is particularly useful in time-sensitive scenarios such as responding to emerging crises or preparing for a critical briefing, where speed and accuracy are paramount.
By breaking down these trends into a number of different categories, such as geographical locations, types of incidents, and involved parties, analysts can access information that is most critical to them.
The tool can be used with whatever filters you desire – for example, the screenshot below shows a summary of incidents that took place in Syria from the launching of the rebel offensive until the immediate fallout of the collapse of the Assad regime:
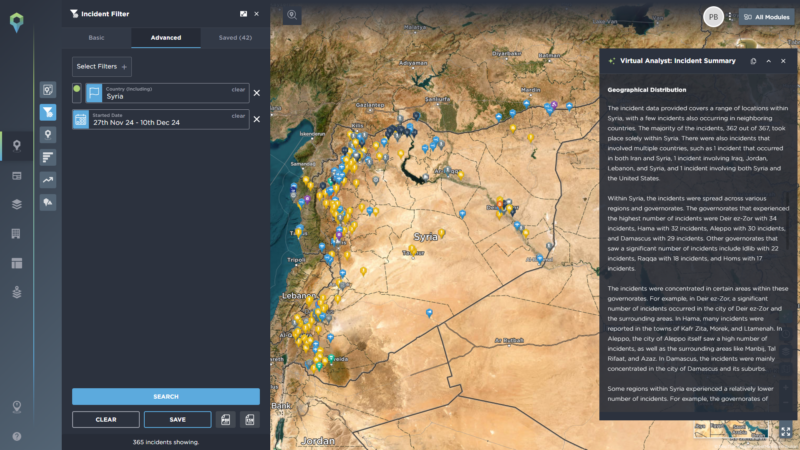
The Virtual Analyst quickly summarizes complex situations in an easy to digest and understand format
Alternatively, here is a summary of incidents involving a firearm in the USA in the past 48 hours:
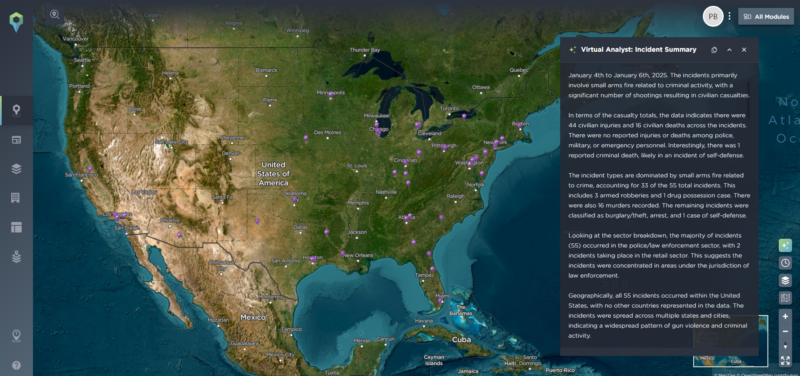
The Virtual Analyst will break down the threat intelligence data into a number of different categories, from types of incident to geographical distribution, identifying key trends and patterns in each section
By reducing cognitive overload, automating repetitive and mentally-draining tasks, and speeding up data analysis and processing, analysts can instead allocate more time to more important tasks, such as strategic planning and threat mitigation. And because the Virtual Analyst is powered by data that has been evaluated, verified and mapped by human experts, the risk of hallucinations and discrepancies is significantly reduced, allowing users to feel confident in the insights it provides. In doing so, the Virtual Analyst bridges the gap between data and actionable intelligence, ensuring users can navigate complex threat landscapes with greater confidence and effectiveness.
To learn more about the Virtual Analyst tool, and how it supports our wider threat intelligence offering, reach out to a member of the team today.






